Why Digital Signatures Don’t Provide Privacy
Digital signatures are a cornerstone of modern cryptography.
They help to ensure the authenticity, integrity, and non-repudiation of digital communications.
But while they excel at proving identity and verifying that data hasn't been tampered with, digital signatures do not provide privacy.
Here's why:
How digital signatures work
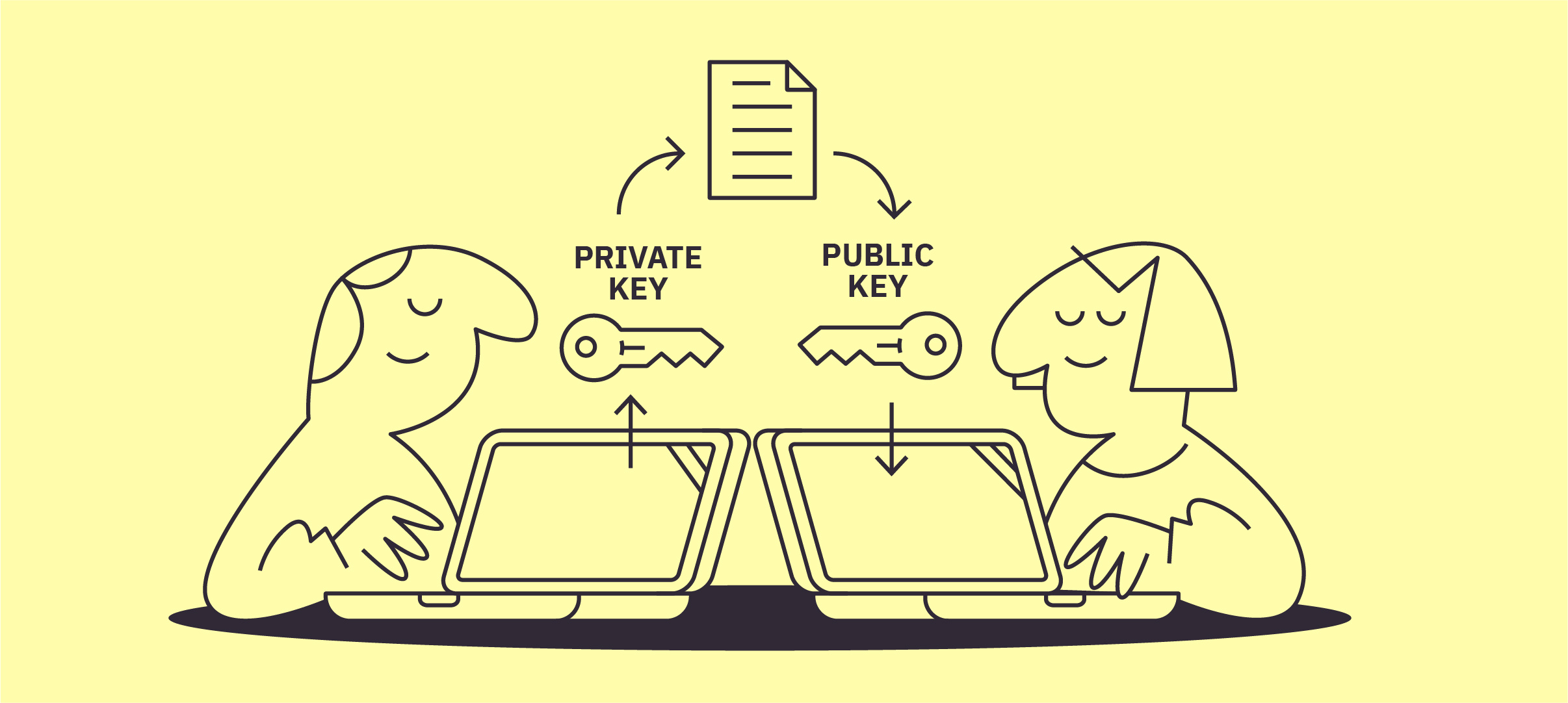
Digital signatures are designed to authenticate a message and link it to the sender, much like a handwritten signature.
They are based on asymmetric cryptography, which involves two mathematically connected keys: a private key and a public key.
- The sender uses their private key to sign a message by encrypting a hash of the message. This creates a digital signature.
- Others can then use the sender’s public key to decrypt the signature and verify the hash. If the hash matches one independently calculated from the message, the signature is valid, which confirms the sender's identity and the integrity of the message.
This mechanism ensures the message hasn’t been altered and provides proof of the sender’s identity.
However, the process does not involve hiding the content of the message.
No encryption
Digital signatures operate on plaintext or its hash.
This makes the message readable by anyone who can access it. This is different from encryption, which hides the data to prevent unauthorized access.
Public verification
A digital signature can be verified by anyone with the sender's public key.
While this ensures transparency and trust, it also means the signature and the associated message are not private.
Identity is traceable
Digital signatures inherently link the signer’s identity to the message through their key pair. This transparency is essential for trust and fulfills the purpose of digital signatures.
Ensuring both privacy and integrity
While digital signatures ensure authenticity and integrity, they don’t obscure content or prevent tracking. Achieving both privacy and authenticity requires additional measures, such as encryption or blind signatures. Blind signatures allow a message to be disguised before being signed, enabling verification without exposing the original content. This is particularly valuable in privacy-focused applications, such as anonymous voting and digital cash systems.



