3 ways to improve the MitID user experience

Suppose you have already integrated the Danish MitID into your web or mobile app. In that case, chances are you already know it's not that complicated.
However, you may also have noticed that some users will get lost during login or sign-in. In these situations, there are ways to improve the overall end-user experience while at the same time making the process more secure.
Follow the advice below to optimize the MitID user experience, increase the number of successful logins and ultimately deny an entire class of phishing attacks through social engineering.
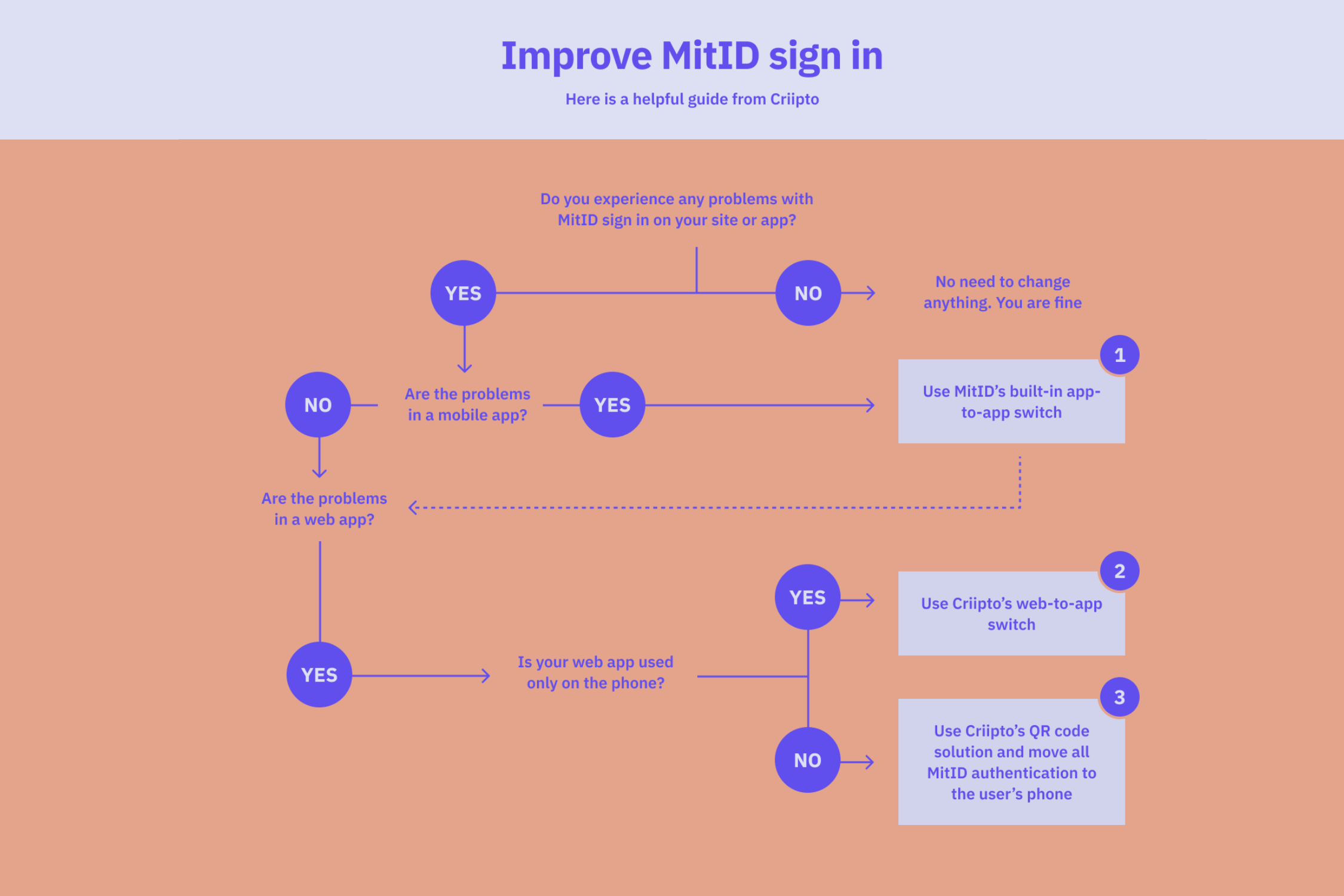
In the following, we outline the different scenarios and what you may do to improve end-user experience and security. Both through built-in MitID functionality and some additional integration options you may choose to implement.
Use MitID in your applications
Integrating MitID to allow end-users to log into your mobile and web apps is not hard. You must find an official MitID broker that suits your specific needs, but no matter which you choose, you'll be fine as long as your technology stack supports OpenID Connect (any sufficient, up-to-date platform and programming framework does). Criipto is one such certified, official MitID broker.
Once you have integrated MitID from a technical perspective, the finer details of the user experience will surface if you dig a bit deeper. Some of the UX issues include the following:
Users get lost on their phones as they leave your app or website to locate the MitID app and make it back to you after completing the MitID authentication.
You have implemented MitID app-switch in your native apps, should you have any. However, users still get lost in your web app, as web-to-MitID app-switch is not found in the standard MitID experience.
Some users may struggle when using MitID on their computer and then locating and completing the MitID app on their phones to complete the process. For security reasons, the MitID app does not give itself away with any notifications.
You, and the well-versed user, may be concerned about the risk of phishing with MitID (and its predecessor, NemID). For a short while, this was a story in Danish media. Now, it's largely forgotten, and not much has changed.
Below we address how leveraging built-in MitID functionality and topping it with additional measures can remedy some of these concerns.
The above diagram shows your three options in condensed form.
Use app-switching to avoid losing the user
Suppose you have a significant percentage of your users on mobile devices. Do you build native apps for iOS and Android? Or do you build a single responsive web application for all form factors?
1. App-switching from native apps
If you're building a native app for Android or iOS, you'll want to ensure the user doesn't get lost during login. If they have to locate the MitID app manually, they may forget or fail to find their way back to your app after the login is complete. The solution to this is the MitID-supported app-switch feature. Exactly how to implement the app-switch depends on your MitID broker, but it should be simple enough as built into the MitID core.
Your native app is able to detect whether MitID is installed on the device. And then, with at least a broker like Criipto, it's a matter of [passing along the correct callback URL and a login hint] (https://docs.criipto.com/verify/guides/appswitch/) indicating you want app-switch.
2. App-switching from a web app on the phone
If you're building a - typically responsive - web app for the browser, MitID does not offer built-in support for app-switching. Instead, you must use the built-in app-to-app switching feature of MitID but with a few caveats. For example, you can't, from a web app, detect if MitID is actually installed on the device. Such detection is only possible from a native app.
It's a bit tricky to make it work from the browser to the MitID app and then back to the browser again. It will require your MitID broker's participation to make it work, but if you use Criipto, web-to-app switching and back are supported out of the box.
3. Eliminate phishing attacks
Finally, one thing that has plagued two-factor authentication solutions, like MitID and many others before that, is the risk of phishing attacks. A phishing attack on MitID is a type of identity attack where the perpetrator initiates the login on their computer and then tricks you into approving it in the MitID app.
There are basically two ways that the bad guys do this:
A) Social engineering attacks, where the perpetrator somehow gets hold of your MitID username. He will enter your username on some site, for example, your bank, and then call you and trick you into opening the MitID app and approving the login. The fraudster is now stealing your money!
B) Technical attacks, where the perpetrator sets up a site that looks like your bank (and has a domain name that could be your bank). You're then lured to the fake site, and after entering your username, the perpetrator immediately enters the username on the real bank's site. The user will now, unsuspectingly, open the MitID app and approve the login. Again, the fraudster is stealing your money!
The first one, the social engineering attack, may be eliminated entirely by technical means. With Criipto, this QR code is used to ensure that the phone with the MitID app is close to the computer screen where the login is occurring. The small video demonstrates how a QR code on a website is used to transfer the login to the user's personal phone.
See how the QR-code works in the video below
The second attack, the technical attack, can be made more complicated to pull off but can't be eliminated using today's options. (An NFC connection between the computer browser and the phone would!) The ever-changing QR code can't just be screenshot and used on a fake phishing site. But with technical proficiency, it would still be possible to stream a QR code from one site, say, the real web bank, to a fake site.
Based on Criipto's experience, it's possible to build an even more secure login process while also increasing ease of use. But do note that users have to start scanning QR codes instead of the usual MitID experience to make this successful.
Bottom line: Guide and educate your users
If you develop a native app, you should implement app-to-app switching immediately. All MitID brokers except NemLog-in support this.
If you develop web applications, consider the other initiatives described. They will require collaboration with your broker as it must fit into the actual login flow. And, if you would use Criipto as your MitID broker, then all these measures are already implemented for you, ready to be turned on for your applications.
As described, it's possible to make MitID easier to use in some scenarios. It's even possible to reduce the attack surface you expose if you use QR codes to transfer all data entry and actions during login to the personal phone.
Finally, no matter what you do to keep your users on the narrow path to a successful and legitimate login, you must always remind them never to approve a MitID login by request from somebody else. MitID is strictly personal and should stay so.
Criipto as MitID broker
Criipto is an official, certified MitID broker and currently serves many large and small companies. Criipto is built by developers for developers and provides extensive customization and extensibility options for you to create the on-brand experience your users will appreciate.
Reach out to our MitID experts to take advantage of the app-switch and QR code solution in your site or app.


